Reading Time: 4 minutes
In this tutorial ” How to check TLS/SSL certificate expiration date from Linux CLI ” we will guide you on how to validate TLS / SSL certificate expiry date using CLI. Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), play a crucial role in securing data transmissions over the internet. Monitoring the expiration dates of TLS/SSL certificates is vital for maintaining a secure online environment. In this guide, we’ll explore how to check TLS/SSL certificate expiration dates using the Linux Command Line Interface (CLI). Secure your web applications with ease by learning how to check TLS/SSL certificate expiration dates from the Linux CLI. Our guide provides step-by-step instructions, Bash scripts, and best practices for maintaining a robust security posture.
Table of Contents
What is SSL
SSL or secure socket layer is an encryption-based internet security protocol. It was invented in the year 1995 by Netscape and its purpose of ensure privacy, authentication, and data integrity in Internet communications. SSL is the predecessor to the modern encryption used.
I have written a detailed tutorial for TLS and SSL, Please read here.
What is TLS
TLS is a secure communication protocol that enables encryption and authentication, and this was true for SSL before it was deprecated. TLS and SSL both use digital certificates that facilitate the handshake process and establish encrypted communications between a browser and a web server.
TLS is the direct successor to SSL, and all versions of SSL are now deprecated. However, it’s common to find the term SSL describing a TLS connection. In most cases, the terms SSL and SSL/TLS both refer to the TLS protocol and TLS certificates.
TLS certificates mainly include the following details:
- Domain Name
- Organization
- The name of the issuing CA
- Subdomains
- Issue Date
- Expiry Date
- The public key
- The digital signature by the CA
How to check TLS/SSL certificate expiration date from Linux CLI
You should have openssl command installed in your server or client machine, If you do not have openssl package installed, Please consider installing it, Please follow the tutorial here.
Commands to Check SSL Expiry Date
Commands
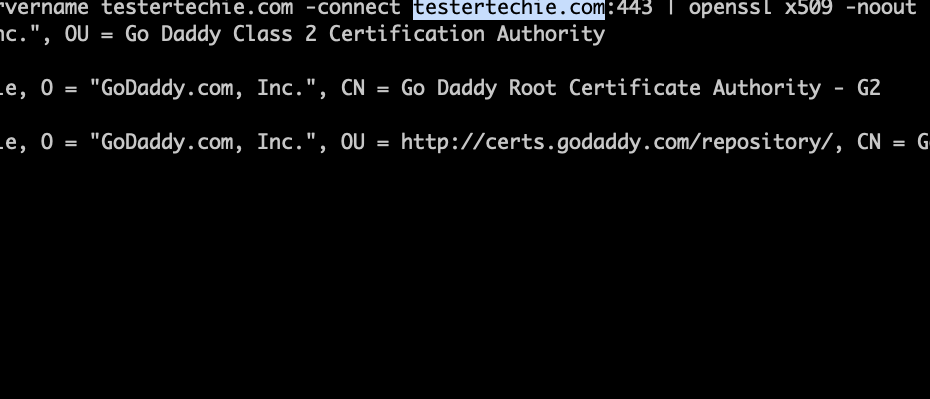
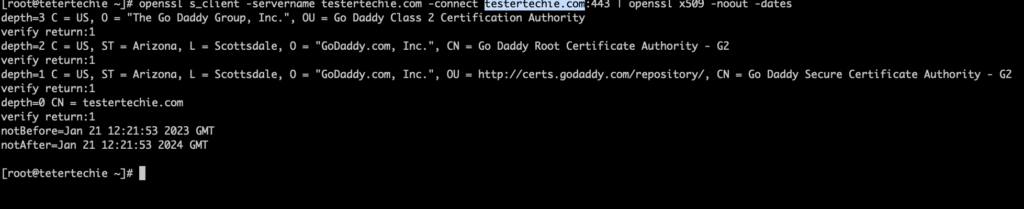
$ openssl s_client -servername testertechie.com -connect testertechie.com:443 | openssl x509 -noout -dates
Commands Explanation:
$ openssl s_client -servername <Domain(FQDN)> -connect <Domain>:443 | openssl x509 -noout -dates
Domain: You should mention the Fully Qualified Domain Name (FQDN ) of your website, In this case, our domain is testertechie.com hence use the same.
Port: You can use the 443 port which is the HTTPS port. HTTP port is 80
Note: The main command is OpenSSL
Check Expiry Date – IP Address
Commands: $ openssl s_client -servername 18.118.64.254 -connect 18.118.64.254:443 | openssl x509 -noout -dates
[root@tetertechie ~]# openssl s_client -servername 18.118.64.254 -connect 18.118.64.254:443 | openssl x509 -noout -dates
depth=3 C = US, O = “The Go Daddy Group, Inc.”, OU = Go Daddy Class 2 Certification Authority
verify return:1
depth=2 C = US, ST = Arizona, L = Scottsdale, O = “GoDaddy.com, Inc.”, CN = Go Daddy Root Certificate Authority – G2
verify return:1
depth=1 C = US, ST = Arizona, L = Scottsdale, O = “GoDaddy.com, Inc.”, OU = http://certs.godaddy.com/repository/, CN = Go Daddy Secure Certificate Authority – G2
verify return:1
depth=0 CN = testertechie.com
verify return:1
notBefore=Jan 21 12:21:53 2023 GMT
notAfter=Jan 21 12:21:53 2024 GMT
[root@tetertechie ~]#
Commands Explanation:
In this above example, we used the IP Address 18.118.64.254 instead of FQDN testertechie.com. Other options are the same as above. You can use the same port 433.
You can also set domain and port as variables and then run openssl command, See the below example
Open bash / Terminal prompt and set variable.
$ domain="testertechie.com"
$ port="443"
Commands
$ openssl s_client -servername $domain -connect $domain:$port | openssl x509 -noout -dates
Method 2
Finding the SSL certificate expiration date using a PEM-encoded certificate file
$ openssl s_client -servername $domain -connect $domain:$port | openssl x509 > ./SSL.cert
In this method, you can set domain and port variables like the above steps. We are downloading an SSL certificate then we will use the same certificate to find out the expiry date.
Use the Below Command to view Expiry Data.
$ openssl x509 -enddate -noout -in ./SSL.cert
[root@tetertechie ~]# openssl x509 -enddate -noout -in ./SSL.cert
notAfter=Jan 21 12:21:53 2024 GMT
[root@tetertechie ~]#
Best Practices for TLS/SSL Certificate Management
- Regular Renewal and Rotation:
- Emphasize the importance of regularly renewing certificates and rotating cryptographic keys to maintain a robust security posture.
- Utilizing Certificate Authorities (CAs):
- Recommend obtaining TLS/SSL certificates from reputable Certificate Authorities, ensuring trustworthiness and widespread recognition by browsers.
Automating Certificate Expiry Checks:
#!/bin/bash
DOMAIN="example.com"
EXPIRY_DATE=$(openssl s_client -connect $DOMAIN:443 -servername $DOMAIN < /dev/null 2>/dev/null | openssl x509 -noout -dates | grep "notAfter" | cut -d= -f2)
TODAY=$(date -d "now" +%s)
EXPIRY=$(date -d "$EXPIRY_DATE" +%s)
DAYS_LEFT=$(( (EXPIRY - TODAY) / 86400 ))
if [ $DAYS_LEFT -lt 30 ]; then
echo "TLS/SSL certificate for $DOMAIN is expiring in $DAYS_LEFT days. Renew it soon."
else
echo "TLS/SSL certificate for $DOMAIN is valid for $DAYS_LEFT days."
fi
Q: How can I check TLS/SSL certificate expiration dates from the Linux CLI?
A: Mastering TLS/SSL Certificate Checks on Linux CLI: A Scannable Guide
- Q: Why is monitoring TLS/SSL certificate expiration crucial for web security?
- A: Regular checks ensure ongoing security, preventing potential issues that may arise from expired certificates in web applications.
- Q: What is the OpenSSL command for checking TLS/SSL certificate expiration from the Linux CLI?
- A: Utilize the following OpenSSL command for a direct check:bashCopy code
openssl s_client -connect example.com:443 -servername example.com < /dev/null 2>/dev/null | openssl x509 -noout -dates
- A: Utilize the following OpenSSL command for a direct check:bashCopy code
- Q: Can I automate TLS/SSL certificate checks on Linux?
- A: Absolutely! Use a Bash script to automate periodic checks, providing alerts for certificates with approaching expiration dates.
- Q: How can I integrate TLS/SSL certificate checks into monitoring tools like Nagios or Prometheus?
- A: Enhance visibility by integrating checks into monitoring tools, ensuring proactive management of TLS/SSL certificate expiration.
- Q: What are the best practices for TLS/SSL certificate management?
- A: Regular renewal, key rotation, and obtaining certificates from reputable Certificate Authorities are key best practices for robust TLS/SSL certificate management.
Conclusion:
We hope you are able to view SSL expiry date using the ” How to check TLS/SSL certificate expiration date from Linux CLI ” tutorial. If you have any question on How to check TLS/SSL certificate expiration date from Linux CLI, Please write to us. Regularly checking TLS/SSL certificate expiration dates is a fundamental practice in maintaining a secure online presence. By leveraging the Linux CLI, organizations can automate these checks, proactively address potential issues, and ensure the continuous security of their web applications and services.