Reading Time: 5 minutes
This tutorial will guide you on How to use different Ansible variables with examples. You can use Ansible variables to manage differences between hosts. Using Ansible, you can execute tasks and playbooks on multiple different systems with a single command. To represent the variations among those different systems, you can create variables with standard YAML syntax, including lists and dictionaries. You must define these variables in your playbooks, in your, Inventory in reusable files or roles, or at the command line. You can also create variables during a playbook run by registering the return value or values of a task as a new variable.
After you create variables, either by defining them in a file, passing them at the command line, or registering the return value or values of a task as a new variable, you can use those variables in module arguments, in conditional “when” statements, in templates, and in loops. The ansible-examples github repository contains many examples of using variables in Ansible.
Once you understand the concepts and examples on this page, read about Ansible facts, which are variables you retrieve from remote systems.
If you have not installed Ansible yet, Install “How to install Ansible“
Table of Contents
How to use different Ansible variables with examples
Create playbook
—
– hosts: all
remote_user: adminuser
serial: 2
become_method: sudo
become_user: root
vars:
var1: [Asia, India, Etc]
tasks:
– name: My Variable
debug:
msg: ‘{{ item }} ‘
with_items:
– “{{ var1[0] }}”
- — = This is starting of yaml file
- remote_user = You can mention the username of remote hosts.
- serial: 2 = This is not mandatory to use however you can run the playbook on 2 nodes together and the next set of nodes will be picked automatically.
- become_method: This is used for privilege
- become_user: This is used to switch user
How to define an ansible variable
- vars: You should use the keyword “vars”
- var1: [Asia, India, Etc] = This is actual variable
How to create an ansible task
- tasks: – This is the syntax to define the task
- – name: My Variable: Give the name of the task
- debug: Use debug
- msg: ‘{{ item }} ‘ Use msg & item is used to look for all items assigned to a variable
- with_items: This is like for loop
- – “{{ var1[0] }}” – It prints 0th element of variable
---
- hosts: all
remote_user: adminuser
serial: 2
become_method: sudo
become_user: root
vars:
var1: [Asia, India, Etc]
tasks:
- name: My Debugger
debug:
msg: '{{ item }} '
with_items:
- "{{ var1[0] }}" How to run ansible-playbook
ansible-playbook -i hostfile variable1.yaml --ask-pass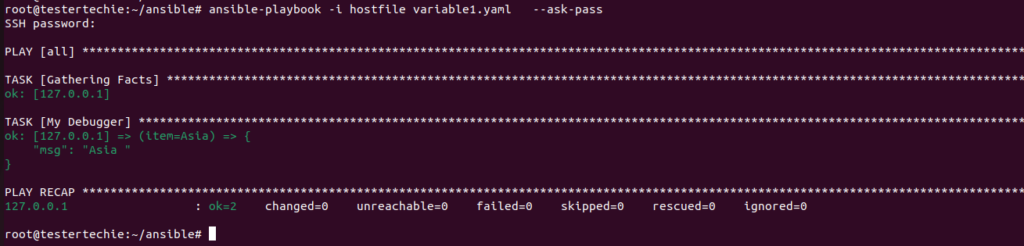
If you need to get all variables, Replace – “{{ var1 }}”
TASK [Gathering Facts] ************************************************************************************************************************************************************************************
ok: [127.0.0.1]
TASK [My Debugger] ****************************************************************************************************************************************************************************************
ok: [127.0.0.1] => (item=Asia) => {
“msg”: “Asia ”
}
ok: [127.0.0.1] => (item=India) => {
“msg”: “India ”
}
ok: [127.0.0.1] => (item=Etc) => {
“msg”: “Etc ”
}
PLAY RECAP ************************************************************************************************************************************************************************************************
127.0.0.1 : ok=2 changed=0 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
You can follow the full tutorial on How To Use Ansible
This concluded tutorial “How to use different Ansible variables with examples”
If you have any questions on How to use different Ansible variables with examples, Please write to us.
You can read more on the Ansible Official website
How can Ansible be used for compliance automation and reporting in IT environments?
Ansible can be a powerful tool for compliance automation and reporting in IT environments. Compliance automation ensures that systems adhere to established security policies, regulatory standards, and industry best practices. Ansible helps automate the enforcement of configurations, assess compliance, and generate reports. Here’s how you can use Ansible for compliance automation and reporting:
1. Define Compliance Policies:
- Clearly define your compliance policies based on regulatory requirements, security standards, and organizational policies. This includes configuration settings, security controls, and other relevant parameters.
2. Ansible Playbooks for Configuration Management:
- Create Ansible playbooks to enforce and maintain compliant configurations. These playbooks should define the desired state of systems based on the compliance policies.
yamlCopy code
--- - name: Ensure Compliance hosts: all tasks: - name: Configure Security Settings template: src: security_settings.j2 dest: /etc/security_settings.conf notify: Restart Services handlers: - name: Restart Services service: name: my_service state: restarted
3. Incorporate Ansible Roles:
- Organize your playbooks using Ansible roles, making it easier to manage and reuse configurations across different systems. Roles enhance modularity and maintainability.
4. Use Ansible Vault for Sensitive Data:
- For handling sensitive information like passwords or encryption keys, use Ansible Vault to encrypt variables within playbooks. This ensures secure handling of critical information.
5. Ansible Galaxy for Community Roles:
- Explore Ansible Galaxy for community-contributed roles that align with compliance requirements. This can save time and provide well-tested configurations.
6. Run Compliance Checks:
- Develop Ansible playbooks or roles specifically for compliance checks. These tasks can assess the current state of systems against predefined compliance policies without making changes.
yamlCopy code
--- - name: Check Compliance hosts: all tasks: - name: Verify Security Settings shell: cat /etc/security_settings.conf register: security_settings_result - name: Fail if Non-Compliant fail: msg: "Non-compliant security settings detected" when: "'expected_value' not in security_settings_result.stdout"
7. Ansible Modules for Assessment:
- Utilize Ansible modules relevant to compliance assessments, such as
command,shell, or custom modules designed for specific checks.
8. Store Compliance Data:
- Store compliance data in structured formats or databases for future analysis. This data can include the results of compliance checks, configurations, and historical records.
9. Generate Compliance Reports:
- Develop Ansible playbooks or scripts to generate compliance reports based on the stored data. These reports can highlight areas of non-compliance, changes over time, and overall adherence to policies.
10. Custom Report Templates:
- Create custom report templates using tools like Jinja2 or other templating engines to present compliance data in a format suitable for stakeholders and auditors.
11. Integrate with CI/CD Pipelines:
- Integrate compliance checks and configurations into your CI/CD pipelines. This ensures that compliance is continuously validated as part of the development and deployment processes.
12. Notify on Non-Compliance:
- Configure Ansible to send notifications when non-compliance is detected. This can include email alerts, messages to chat platforms, or integration with monitoring systems.
13. Regular Auditing and Review:
- Schedule regular audits and reviews of compliance configurations and reports. Keep playbooks and policies up-to-date with evolving security standards.
14. Collaborate with Security Teams:
- Collaborate with security teams to align Ansible configurations with security policies. This ensures that compliance automation efforts align with organizational security objectives.
15. Document Compliance Processes:
- Document compliance automation processes, including playbooks, roles, policies, and reporting mechanisms. This documentation is essential for transparency, auditability, and knowledge sharing.
By integrating compliance automation into your Ansible workflows, you can systematically enforce security policies, assess compliance, and generate reports to demonstrate adherence to regulatory requirements and best practices. This approach ensures a proactive and automated approach to maintaining a compliant IT environment.
You can find all Ansible tutorials on this page.
You can find Jenkins Tutorials on this page
You can also find all Video Tutorial on Youtube
Conclusion:
Follow us on Facebook Twitter X Reddit Quora Linkedin Tubmblr Youtube