Reading Time: 10 minutes >
In this tutorial, you will learn How to create Ansible Inventory and how to use it. Streamline your IT operations with Ansible, an open-source automation tool. This tutorial guides you through Ansible installation, inventory creation, ad-hoc commands, and scaling infrastructure efficiently. Enhance your network automation and discover how Ansible Tower elevates your automation workflows
Table of Contents
Ansible Inventory – It is a file or inventory which can be used to track servers, Devices hostnames, or IPs so you can run or push ansible commands / Playbook from Ansible Master Node
The inventory configuration file is /etc/ansible/hosts and this is the main default config file however if you do not have the privilege of /etc/ directory you can create inventory in any directory.
When you create a custom inventory you need to use -i parameter so ansible can understand that this inventory to use used.
If you have not installed Ansible, You can read more on How to install ansible
- Ansible simplifies IT automation, emphasizing security and ease of use.
- Dynamic inventories enable seamless tracking and management of servers.
- Ansible Tower centralizes control, offering role-based access, job templates, and orchestration.
- Security measures include SSH transport, credential encryption, and identity management.
How to create Ansible Inventory
Navigate to your home directory
run command $ cd /home/username
Note: username is your username$ cd /home/adminuser
Create empty file
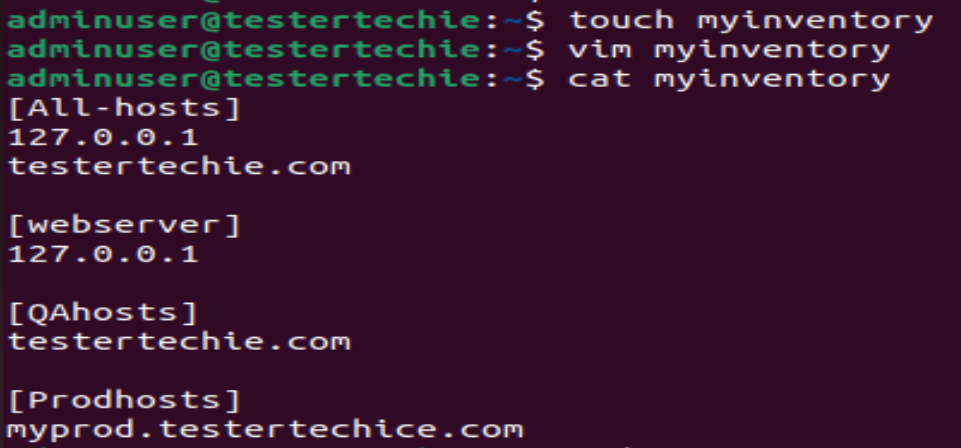
$ touch myinventory
$ vim myinventory
[Allhosts]
127.0.0.1
testertechie.com
[webserver]
127.0.0.1
[QAhosts]
testertechie.com
[Prodhosts]
myprod.testertechice.com
Save file Esc:wq!
You can see [Allhosts] , [webserver] , [QAhosts], [Prodhosts]
These are called groups under inventory , You can either mention IP address of hosts or FQDN
[Allhosts] – You can mention all hosts IP/Name .
[webserver] – You can mention all of your web hosts
[QAhosts] – This can have only QA or non prod hosts

Please watch the complete steps “How to Create Ansible Inventory“
What security considerations should be taken into account when using Ansible?
When using Ansible, it’s crucial to consider security measures to protect sensitive information, ensure secure communication, and maintain the integrity of your automation workflows. Here are key security considerations when working with Ansible:
1. Secure Communication:
- Use SSH as the default transport for Ansible, which ensures encrypted communication between the Ansible control node and managed hosts.
- Avoid using insecure protocols like telnet or unencrypted HTTP.
2. Credential Management:
- Use Ansible Vault to encrypt sensitive data, such as passwords and API keys, within playbooks and roles.
- Avoid storing sensitive information directly in plain text within playbooks.
3. Identity and Access Management:
- Implement proper identity and access controls. Use strong, unique passwords for Ansible control node access.
- Limit access to Ansible control nodes to authorized personnel only.
4. Privilege Escalation:
- Use
becomeorsudowith caution. Limit the use of privilege escalation to tasks that require elevated privileges, and only grant necessary permissions to Ansible users.
5. Securing Ansible Configuration Files:
- Ensure that Ansible configuration files (ansible.cfg) are secured and only accessible by authorized users.
- Avoid exposing sensitive information, such as passwords, in plain text within configuration files.
6. Host Key Verification:
- Enable host key verification to ensure that Ansible only connects to trusted hosts. This helps prevent man-in-the-middle attacks.
7. Audit Logging:
- Enable and regularly review Ansible logs. Audit logs can help identify unauthorized access, changes, or suspicious activities.
8. Update Ansible Versions:
- Keep Ansible and related components up to date to benefit from security patches and improvements. Regularly check for updates and security advisories.
9. Secure Dynamic Inventories:
- If using dynamic inventories, secure the scripts or sources used to generate inventory data. Ensure that sensitive information is handled securely within dynamic inventory scripts.
10. Network Segmentation:
- Consider network segmentation to isolate Ansible control nodes from critical infrastructure. Limit network exposure and potential attack surfaces.
11. Secure Storage for Ansible Vault Passwords:
- Store Ansible Vault passwords securely. Consider using a dedicated secrets management solution to protect encryption keys and passwords.
12. Security Automation and Scanning:
- Integrate security scanning tools into your CI/CD pipeline to scan Ansible playbooks and roles for security vulnerabilities and compliance issues.
13. Role-Based Access Control (RBAC):
- If using Ansible Tower or AWX, implement RBAC to control access to inventories, playbooks, and other resources. Define roles with the principle of least privilege.
14. Monitoring and Alerting:
- Set up monitoring and alerting for Ansible control node activities. Monitor for unusual patterns or potential security incidents.
15. Documentation and Training:
- Document security best practices for Ansible usage within your organization. Provide training for Ansible users on security considerations and best practices.
By incorporating these security measures into your Ansible workflows, you can mitigate potential risks and enhance the overall security posture of your automation environment. Regularly review and update security practices to adapt to evolving threats and industry best practices.
How does Ansible support integration with containerization technologies like Docker?
Ansible provides robust support for integration with containerization technologies, with Docker being one of the primary platforms. This integration allows users to automate the deployment, configuration, and management of Docker containers and the surrounding infrastructure. Here’s how Ansible supports Docker integration:
1. Docker Modules:
- Ansible includes a set of Docker-specific modules that allow users to interact with Docker and manage containers. Some key modules include:
docker_image: Builds, loads, or removes Docker images.docker_container: Creates, starts, stops, and removes Docker containers.docker_network: Manages Docker networks.docker_volume: Manages Docker volumes.
2. Docker Connection Plugin:
- Ansible uses a connection plugin to interact with remote hosts. The
dockerconnection plugin enables Ansible to connect to Docker containers on a remote host. This is useful for managing containers on a target system without requiring SSH.
3. Docker Compose Module:
- Ansible provides the
docker_composemodule to manage Docker Compose configurations. This module allows users to define and deploy multi-container applications using Docker Compose files.
4. Container Orchestration Platforms:
- Ansible seamlessly integrates with container orchestration platforms like Kubernetes, OpenShift, and Docker Swarm. Users can use Ansible playbooks to automate the deployment and management of containerized applications on these platforms.
5. Docker-Py Library:
- Ansible relies on the Docker-Py library, a Python client for Docker, to communicate with the Docker API. This library provides a Pythonic interface for interacting with Docker, and Ansible utilizes it to execute Docker-related tasks.
6. Docker Facts:
- Ansible gathers facts about Docker installations on managed hosts. These facts, available through the
ansible_facts.docker_versionvariable, include details about the installed Docker version, storage drivers, and more.
7. Docker Image and Container Handling:
- Ansible playbooks can define tasks to build Docker images, push them to registries, and pull them onto target hosts. Similarly, tasks can create, start, stop, or remove Docker containers based on defined specifications.
8. Dynamic Inventory for Docker:
- Ansible supports dynamic inventories for Docker, allowing users to automatically discover and manage Docker hosts. This is particularly useful in dynamic or containerized environments.
9. Container Health Checks:
- Ansible playbooks can include tasks to perform health checks on containers, ensuring that applications within the containers are running as expected.
10. Integration with Other Ansible Features:
- Ansible’s features such as variables, templates, and conditionals can be applied to Docker-related tasks, enabling dynamic and flexible configurations for containerized environments.
11. Docker Swarm and Kubernetes Modules:
- Ansible includes modules specifically for managing Docker Swarm clusters (
docker_swarmmodule) and Kubernetes clusters (k8smodule), offering comprehensive support for container orchestration.
By leveraging these features, Ansible provides a comprehensive and flexible solution for managing Docker containers and integrating seamlessly with various containerization technologies. Whether working with individual containers or orchestrating containerized applications in complex environments, Ansible simplifies the automation and configuration management tasks associated with Docker.
What are the key features of Ansible Tower and how does it enhance automation?
Ansible Tower, now known as Red Hat Ansible Automation Platform, is a web-based automation platform that complements Ansible by providing additional features for centralized management, orchestration, and scaling of automation workflows. Here are the key features of Ansible Tower and how it enhances automation:
1. Web-Based User Interface:
- Ansible Tower offers a user-friendly web interface that allows users to visualize and manage their Ansible automation workflows. This interface simplifies the creation, scheduling, and monitoring of automation jobs.
2. Role-Based Access Control (RBAC):
- RBAC in Ansible Tower enables administrators to define roles and permissions for users and teams. This granular control ensures that only authorized users can access and modify specific inventories, playbooks, and other resources.
3. Job Templates:
- Job Templates in Ansible Tower allow users to define, schedule, and launch automation jobs easily. They encapsulate Ansible playbooks, inventory, and credentials, providing a streamlined way to execute tasks.
4. Inventory Management:
- Ansible Tower centralizes inventory management, making it easy to organize and maintain host inventories. Dynamic inventories can be automatically generated based on external sources like cloud providers or custom scripts.
5. Credentials Management:
- Ansible Tower securely manages credentials such as SSH keys, passwords, and API tokens. These credentials can be associated with automation jobs, ensuring secure access to managed systems and services.
6. Workflow Editor:
- The Workflow Editor in Ansible Tower allows users to create complex automation workflows by defining sequences of jobs, dependencies, and conditional logic. This enables the orchestration of multi-step processes.
7. Logging and Auditing:
- Ansible Tower logs all job execution details, providing a comprehensive audit trail. This logging facilitates troubleshooting, compliance tracking, and historical analysis of automation activities.
8. Notifications:
- Ansible Tower supports customizable notifications, alerting administrators and users about job status, completion, or failure. Notifications can be sent via email, chat, or integrated with third-party messaging services.
9. API and CLI:
- Ansible Tower provides a RESTful API, allowing integration with external tools and systems. The command-line interface (CLI) offers additional flexibility for automation and scripting.
10. Scaling and Clustering:
- Ansible Tower supports clustering to enhance scalability and high availability. Multiple Tower instances can be configured to work together, distributing the load and ensuring continuous availability.
11. Job Scheduling:
- Automation jobs can be scheduled in Ansible Tower, enabling recurring tasks and time-based executions. This is useful for routine maintenance, backups, and other scheduled operations.
12. Survey Feature:
- Job Templates can include surveys, which are user-friendly forms that prompt users for input before launching a job. This feature allows for dynamic customization of job runs.
13. Integrated Credentials Encryption:
- Ansible Tower encrypts sensitive information, such as credentials and passwords, stored within the system. This enhances security and compliance with data protection standards.
14. Integrated Dashboards and Reports:
- Ansible Tower provides dashboards and reports that offer insights into automation activity, including job status, historical trends, and performance metrics.
By incorporating these features, Ansible Tower enhances automation by providing a centralized, secure, and scalable platform for managing Ansible workflows. It simplifies collaboration, facilitates role-based access control, and offers advanced capabilities for orchestrating complex automation tasks across diverse environments.
How can Ansible be employed for network automation and device configuration?
Ansible is a powerful tool for network automation and device configuration, enabling network engineers to automate repetitive tasks, streamline configurations, and manage network infrastructure efficiently. Here’s how Ansible can be employed for network automation:
1. Network Modules:
- Ansible includes a variety of network modules that support different network devices. Modules like
ios_command,ios_config,nxos_command, andeos_commandallow users to interact with devices from various vendors, including Cisco, Juniper, Arista, and others.
2. Inventory Management:
- Use Ansible’s inventory system to define and organize network devices. Inventories can be static or dynamic, and they can include details like device IP addresses, credentials, and groupings.
3. Playbooks for Configuration Management:
- Create Ansible playbooks to automate device configurations. Playbooks define a series of tasks to be executed on network devices. Tasks can include commands, configuration changes, or checks for compliance.
yamlCopy code
--- - name: Configure Network Devices hosts: network_devices gather_facts: no tasks: - name: Configure Interface ios_config: lines: - interface GigabitEthernet1/0/1 - description Connected to Switch 2 - switchport mode access - switchport access vlan 10 become: yes
4. Variables and Templates:
- Utilize variables and templates in playbooks for dynamic configurations. This allows you to reuse playbooks across different environments and customize configurations based on specific device attributes.
5. Conditional Execution:
- Apply conditional statements in playbooks to execute tasks based on the state of network devices. For example, you can check the current configuration before applying changes to ensure idempotent behavior.
6. Integration with Version Control:
- Store your playbooks in version control systems like Git to track changes, collaborate with team members, and maintain a history of configurations. This facilitates code reviews and rollback options.
7. Role-Based Access Control (RBAC):
- Implement RBAC in Ansible Tower or AWX to control access to playbooks and inventories. Define roles with specific permissions to ensure that only authorized users can execute or modify configurations.
8. Automated Backups:
- Develop Ansible playbooks to automate device configuration backups. Regularly back up configurations to version-controlled repositories, providing a safety net for configuration changes.
9. Integration with Network APIs:
- Ansible can interact with network devices using APIs. Leverage modules like
urito perform HTTP requests to device APIs, enabling advanced automation and integration with RESTful interfaces.
10. Error Handling and Logging:
- Implement error handling in playbooks to gracefully manage failures during configuration changes. Ansible logs provide detailed information for troubleshooting and auditing.
11. Network Testing and Verification:
- Incorporate testing modules in playbooks to verify the state of network devices after configuration changes. Modules like
assertandwait_forcan be used to ensure that configurations are applied successfully.
12. Dynamic Inventories and Device Discovery:
- Use dynamic inventories to automatically discover and manage network devices. This is particularly useful in large and dynamic network environments where devices may be added or removed frequently.
13. Documentation and Comments:
- Include documentation within playbooks and roles. This documentation provides insights into the purpose of configurations, making it easier for team members to understand and collaborate.
By leveraging these features, Ansible becomes a valuable tool for network automation, allowing network engineers to automate routine tasks, maintain consistent configurations, and enhance the overall efficiency and reliability of network infrastructure.
How to use Ansible
Please read more on How to use Ansible
You can find all Ansible tutorials on this page.
You can find Jenkins Tutorials on this page
You can also find all Video Tutorial on Youtube
How to use adhoc command without a playbook
Please read more on How to use adhoc command
Question: How does Ansible contribute to ensuring infrastructure as code (IaC) compliance?
Ansible ensures IaC compliance through declarative syntax, idempotency, version control, RBAC, and integration with external tools. It offers automated testing, policy enforcement, and configuration drift detection, fostering a secure and compliant infrastructure.
We hope you have a basic understanding of How to create an Ansible Inventory however if you have any queries please write us.
Ansible Inventory Official Documentation can be found here
Follow us on Facebook Twitter X Reddit Quora Linkedin Tubmblr Youtube