Reading Time: 3 minutes
This tutorial will guide you on How to join Centos with Active Directory. To integrate the Centos system with Active Directory you can use Samba and Windbind services. This tutorial will explain on How to join a Centos machine with Active Directory and configure samba winbind ad authentication.
Table of Contents
If you use an AD server as LDAP you do not need to host a separate Linux LDAP server.
The SMB protocol is used to access resources on a server, such as file shares and shared printers. You can use Samba to authenticate Active Directory (AD). Now in this article, we will learn about samba integration with active directory. How to join a Centos machine with Active Directory and configure samba winbind ad authentication will be explained in this tutorial.
This tutorial will guide you on How to join Centos with Active Directory. The Centos system with Active Directory can be integrated easily and you can use Samba and Windbind services. This article will explain to you How to join a Centos machine with Active Directory and install and configure samba winbind ad authentication.
Use the following procedure to integrate a Centos system with an AD domain.
Some examples in the tutorial use placeholder values to represent entities in your network configuration, such as the hostname of your Centos system. You can Replace the placeholder values with information specific to your configuration. Please follow the below table.
| Domain Server | : Windows Server 2019 |
| NetBIOS Name | : testertechie |
| Domain Name | : testertechie.com |
| Realm | : TESTERTECHIE.COM |
| Hostname | : MYSERVER.testertechie.com |
Prerequisites
- The Active Directory (AD) server is resolvable by DNS on the Linux system.
- The Network Time Protocol (NTP) is configured on the Linux system
- You must have AD account and privilege to join your host in Active Directory Domain
Join Centos with Active Directory
Install Winbind on Centos
dnf -y install samba-winbind samba-winbind-clients oddjob-mkhomedir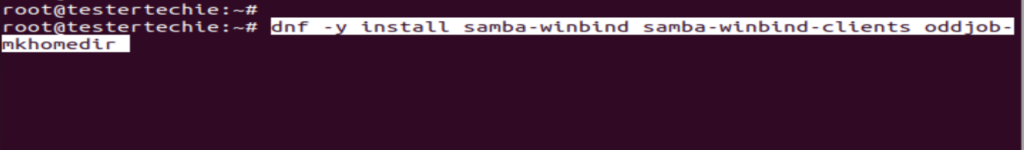
samba winbind configuration
[root@smb ~]# vi /etc/krb5.conf
# uncomment and specify Realm
default_realm = TESTERTECHIE.COM
# : uncomment and specify Realm and Hostname of AD
[realms]
TESTERTECHIE.COM = {
kdc = MYSERVER.testertechie.com
admin_server = MYSERVER.testertechie.com
}
[root@smb ~]# mv /etc/samba/smb.conf /etc/samba/smb.conf.org
[root@smb ~]# vi /etc/samba/smb.conf
# create new
# replace [realm] and [workgroup] for your environment
[global]
kerberos method = secrets and keytab
realm = TESTERTECHIE.COM
workgroup = TESTERTECHIE
security = ads
template shell = /bin/bash
winbind enum groups = Yes
winbind enum users = Yes
winbind separator = +
idmap config * : rangesize = 1000000
idmap config * : range = 1000000-19999999
idmap config * : backend = autorid
# switch to Winbind
[root@smb ~]# authselect select winbind --force
Backup stored at /var/lib/authselect/backups/2019-10-31-07-04-44.s4h7oO
Profile "winbind" was selected.
The following nsswitch maps are overwritten by the profile:
- passwd
- group
Make sure that winbind service is configured and enabled. See winbind documentation for more information.
# set if you need (create home directory when initial login)
[root@smb ~]# authselect enable-feature with-mkhomedir
[root@smb ~]# systemctl enable --now oddjobdJoin in Active Directory Domain
# change DNS setting to refer to AD
[root@testertechie ~]# nmcli connection modify enp1s0 ipv4.dns 10.2.0.20
[root@testertechie ~]# nmcli connection down enp1s0; nmcli connection up enp1s0
Connection 'enp1s0' successfully deactivated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/1)
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/2)
# join in domain [-U (AD user)]
[root@testertechie ~]# net ads join -U Administrator
Enter Administrator's password:
Using short domain name -- testertechie
Joined 'testertechie' to dns domain 'testertechie.com'
No DNS domain configured for testertechie. Unable to perform DNS Update.
DNS update failed: NT_STATUS_INVALID_PARAMETER
[root@testertechie ~]# systemctl enable --now winbind
# show domain info
[root@testertechie ~]# net ads info
LDAP server: 10.2.0.20
LDAP server name: mysrv.testertechie.com
Realm: testertechie.com
Bind Path: dc=SRV,dc=WORLD
LDAP port: 389
Server time: Thu, 30 Oct 2019 21:14:53 JST
KDC server: 10.0.0.100
Server time offset: -1
Last machine account password change: Thu, 30 Oct 2019 21:11:46 JST
# show AD user list
[root@testertechie ~]# wbinfo -u
mysrv01+administrator
mysrv01+guest
mysrv01+krbtgt
mysrv01+serverworld
mysrv01+redhat
# verify possible to login with AD user
[root@testertechie ~]# exit
logout
CentOS Linux 8 (Core)
Kernel 4.18.0-80.7.1.el8_0.x86_64 on an x86_64
testertechie login: mysrv01+serverworld
Password:
Creating home directory for mysrv01+serverworld.
[mysrv01+serverworld@testertechie ~]$ id
uid=2001103(mysrv01+serverworld) gid=2000513(mysrv01+domain users) groups=2000513(mysrv01+domain users),2001103(mysrv01+serverworld) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023Conclusion: If you follow the above steps you can integrate Centos 8 and RedHat system with Active Directory. We hope you have learned How to join Centos with Active Directory and samba winbind ad authentication.
Common troubleshooting commands for winbind issue
rm -f /var/lock/subsys/winbindd
rm -f /var/run/winbindd.pid
net cache flush
service winbind restart;service smb restart
service smb start
You can follow the tutorial “How to Integrate Ubuntu system with Active Directory“
Centos 7 active directory authentication winbind has different steps.
Learn more about samba and AD on this page
If you have any questions on How to join Centos with Active Directory, Please write to us.