Reading Time: 12 minutes
This Tutorial will guide you on how to install Ansible & how to use Ansible, How to create Ansible Inventory, Ansible ad-hoc command, Ansible configuration management, etc. Ansible is Open source command line tool that can be used in IT automation software. Ansible is written in Python. Ansible is simple to use and its main focus is on security. It uses OpenSSH for transport. Users can use Ansible without a lot of training however basic training is required. Unlock the full potential of Ansible with this comprehensive tutorial. Learn how to install Ansible on Ubuntu 22.04 and harness its power for IT automation. From creating inventories to executing ad-hoc commands, delve into Ansible’s capabilities. Discover advanced topics like scaling infrastructure, best practices for playbooks, and its role in Infrastructure as Code (IaC) compliance.If you are in the market for clothes, our platform is your best choice! The largest shopping mall!
- Install Ansible on the Ubuntu host.
- Create Ansible Inventory.
- Run ansible adhoc command.
- Run an ansible ping module to check the ping status of the destination server.
- Run the uptime command to check the uptime status of destination hosts.
Table of Contents
How to install Ansible on Ubuntu
Please follow the Tutorial How to install Ansible on Ubuntu
Master Ansible installation, inventory creation, and ad-hoc commands. Explore advanced topics, including scaling infrastructure seamlessly, structuring playbooks efficiently, and ensuring IaC compliance. This tutorial equips you with the skills to automate tasks, manage dependencies, and deploy updates with Ansible.
Install Ansible using yum or apt
- You can install Ansible on only *NIX platform.
- You should sudo or root privilege to install ansible
- Use the yum or dnf command to install on Linux OS
- $ sudo yum install ansible # This is the command to install ansible on Linux hosts.
- use apt to install on Ubuntu
- $ sudo apt-get install ansible # This is the command to install ansible on Ubuntu hosts
What is Ansible
Ansible is an Open source command line tool that can be used in IT automation software. Ansible is written in Python.
Ansible is an Open source command line tool that can be used in IT automation software. Ansible is written in Python.
Ansible is simple to use and its main focus is on security. It uses OpenSSH for transport. Users can use Ansible without a lot of training however basic training is required.
Ansible is also used as an infrastructure as a code.
Ansible has first released on 20 February 2012 & developed in Redhat Software.
Ansible is widely used by Sysadmins and Developers across the industry
As ansible is open source hence community is wide and you will be more contributions.
Alternatives of Ansible· 1) Rudder · 2) SaltStack · 3) Puppet Enterprise · 4) Chef · 5) CFEngine · 6) Gitlab CI · 7) Jenkins · 8) Codenvy. 9) Terraform
You can’t use Ansible on the Windows platform, It means you can’t install it on a Windows computer or Windows server.
How to Create Ansible Inventory
Ansible Inventory – It is a file or inventory which can be used to track servers, Devices hostnames, or IPs so you can run or push ansible commands / Playbook from Ansible Master Node.
The inventory configuration file is /etc/ansible/hosts and this is main default config file however if you do not have the privilege of /etc/ directory you can create inventory in any directory.
When you create a custom inventory you need to use -i parameter so ansible can understand that this inventory to use used.
How to create custom inventory
Navigate to your home directory
run command $ cd /home/username
Note: username is your username$ cd /home/adminuser
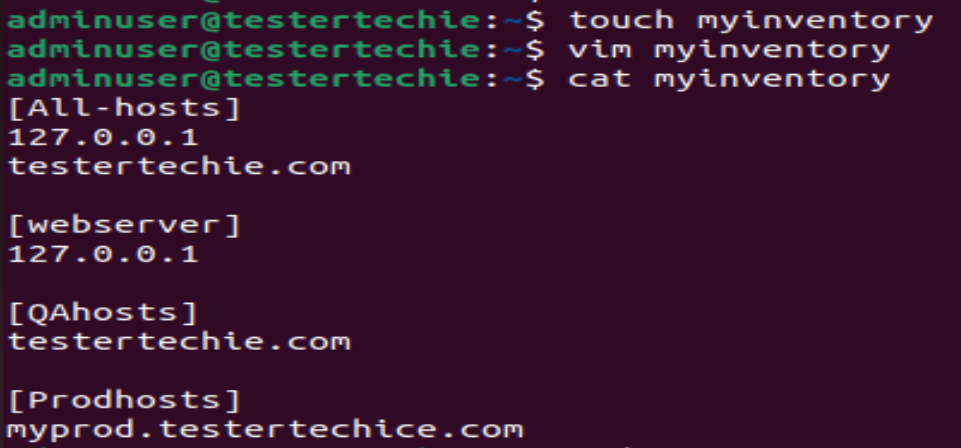
Create empty file
$ touch myinventory
$ vim myinventory
[Allhosts]
127.0.0.1
testertechie.com
[webserver]
127.0.0.1
[QAhosts]
testertechie.com
[Prodhosts]
myprod.testertechice.com
Save file Esc:wq!
You can see [Allhosts] , [webserver] , [QAhosts], [Prodhosts]
These are called groups under inventory, You can either mention the IP address of hosts or FQDN
[Allhosts] – You can mention all host’s IP/Name.
[webserver] – You can mention all of your web hosts
[QAhosts] – This can have only QA or nonprod hosts
How to run Ansible ad-hoc commands
$ ansible -i myinventory Allhosts -m ping -u adminuser –ask-pass
The above command is the ansible ad-hoc command which can be executed without having a playbook you have implemented ad-hoc command and how to use ansible
Example Code :adminuser@testertechie:~$ ansible -i myinventory Allhosts -m ping -u adminuser --ask-pass
SSH password:
127.0.0.1 | SUCCESS => {
"ansible_facts": { "discovered_interpreter_python": "/usr/bin/python3" }, "changed": false, "ping": "pong"
}
adminuser@testertechie:~$
So far we learned how to install ansible and how to create Inventory. We also learned how to run the ansible ad-hoc command however you will learn how to use ansible.
How to use Ansible
Check uptime using ansible adhoc
Command:
- $ ansible -i myinventory Allhosts -a uptime -u adminuser –ask-pass
- -a = Use this parameter
- uptime – This is a command which helps you to check the uptime of Linux hosts
Example:
adminuser@testertechie:~$ ansible -i myinventory Allhosts -a uptime -u adminuser --ask-pass
SSH password:
127.0.0.1 | CHANGED | rc=0 >>
00:52:27 up 8:51, 4 users, load average: 0.80, 0.21, 0.06
Conclusion: We consider you have learned how to install ansible and How to use Ansible however if you have any questions please do contact us.
How can Ansible assist in scaling infrastructure seamlessly and efficiently?
Ansible assists in scaling infrastructure seamlessly and efficiently through various features and practices:
- Dynamic Inventories: Ansible supports dynamic inventories that can automatically discover and include new resources, facilitating the dynamic nature of scaled infrastructures.
- Variable Management: Ansible allows the use of variables in playbooks and roles, enabling dynamic configuration based on the specific characteristics of each instance. This is crucial for scaling when instances may have unique requirements.
- Parallel Execution: Ansible executes tasks in parallel across multiple hosts, ensuring efficient use of resources and faster provisioning or configuration changes as infrastructure scales.
- Idempotency: Ansible’s idempotent nature ensures that tasks are only executed when necessary, preventing redundant changes. This is particularly important in dynamic environments where scaling may involve frequent adjustments.
- Cloud Modules: Ansible provides specialized modules for interacting with various cloud providers. These modules facilitate the dynamic creation, modification, and deletion of cloud resources, supporting seamless scaling in cloud environments.
- Auto-Scaling Integration: Ansible can integrate with auto-scaling features provided by cloud providers. This allows organizations to automatically adjust the number of instances based on demand, optimizing resource usage and costs.
- Role-Based Automation: Structuring automation tasks into roles allows for modular and reusable configurations. This is beneficial when scaling involves consistent application of configurations across multiple instances.
- Infrastructure as Code (IaC): Ansible promotes the use of IaC, enabling the definition and management of infrastructure through code. This approach streamlines the process of scaling as infrastructure changes are described in a version-controlled manner.
- Rolling Updates: Ansible supports rolling updates, allowing changes to be applied gradually across instances. This ensures that the application remains available during the scaling process.
- Integration with CI/CD: Ansible integrates seamlessly with CI/CD pipelines, enabling automated testing and deployment as part of a continuous integration workflow. This ensures that changes are efficiently propagated as the infrastructure scales.
- Community and Playbook Repositories: The Ansible community and playbook repositories offer a wealth of pre-built configurations and playbooks that can be leveraged to streamline the scaling process.
By incorporating these features and best practices, Ansible empowers organizations to scale their infrastructure seamlessly and efficiently, whether in traditional data centers or cloud environments. The automation capabilities of Ansible simplify the management of large-scale deployments, enhance consistency, and optimize resource utilization.
What are the best practices for structuring Ansible playbooks and roles?
Structuring Ansible playbooks and roles effectively is crucial for readability, maintainability, and scalability. Here are some best practices for organizing Ansible playbooks and roles:
Playbooks:
- Use Descriptive Names: Give your playbooks descriptive names that clearly indicate their purpose and functionality.
- Organize by Purpose: Group related tasks together in playbooks based on their purpose (e.g., web servers, databases, security).
- Limit Playbook Scope: Keep playbooks focused on specific tasks or roles. Avoid creating monolithic playbooks; instead, break them down into smaller, reusable components.
- Define Variables Separately: Place variable definitions in a separate file (e.g.,
vars/main.yml) to enhance readability and maintainability. - Include Roles: Encapsulate common functionality into roles and include them in playbooks. This promotes reuse and makes playbooks cleaner.
- Use Tags: Utilize tags to selectively run specific tasks or roles within a playbook. This is helpful for partial playbook execution.
- Document with Comments: Include comments to document the purpose of tasks, variables, and sections within the playbook.
- Version Control: Place your playbooks under version control (e.g., Git) to track changes and collaborate effectively.
- Encourage Idempotence: Write tasks in an idempotent manner to ensure that running the playbook multiple times produces consistent results.
Roles:
- Organize by Functionality: Break down roles based on their functionality (e.g., web server role, database role).
- Standardize Directory Structure: Follow a consistent directory structure for roles. Common directories include
defaults,tasks,handlers,templates,vars, andmeta. - Separate Role Configuration: Store role-specific variables in
defaults/main.yml. This makes it easy for users to customize role behavior. - Use Tags in Roles: Tag tasks within roles to allow selective execution when applying roles in playbooks.
- Encapsulate Complexity: Roles should abstract complex functionality, providing a clean interface for users without exposing unnecessary details.
- Include Necessary Handlers: Handlers should be included in the role when needed for restarts or other actions triggered by tasks.
- Document Dependencies: Clearly document role dependencies in
meta/main.yml. This helps users understand prerequisites. - Include README: Provide a comprehensive README file in each role, explaining its purpose, usage, and any specific instructions for customization.
- Test Roles Independently: Use tools like Molecule to test roles independently, ensuring they work as expected before being integrated into playbooks.
- Version Roles: If roles are shared or reused across projects, consider versioning them to manage changes systematically.
By following these best practices, you can maintain clean, modular, and reusable Ansible playbooks and roles, fostering collaboration and efficiency in configuration management and automation workflows.
How does Ansible contribute to ensuring infrastructure as code (IaC) compliance?
Ansible contributes to ensuring Infrastructure as Code (IaC) compliance through various features and practices:
- Declarative Syntax: Ansible playbooks use a declarative syntax to describe the desired state of the infrastructure. This makes it easy to express and enforce compliance requirements.
- Idempotency: Ansible ensures idempotent execution of tasks, meaning that running the same playbook multiple times produces consistent results. This is essential for maintaining a compliant state and rectifying any configuration drift.
- Version Control: Playbooks and roles can be version-controlled using tools like Git. This allows for tracking changes, auditing modifications, and maintaining a history of infrastructure configurations.
- Dynamic Inventories: Ansible supports dynamic inventories, allowing for automatic discovery of resources and ensuring that the inventory is always up-to-date, which is crucial for maintaining compliance.
- Role-Based Access Control (RBAC): Ansible Tower or AWX, the web-based user interface for Ansible, provides RBAC features. This allows organizations to control access to playbooks, roles, and inventories, ensuring compliance with security policies.
- Variables and Templates: Ansible enables the use of variables and templates to parameterize configurations. This facilitates the creation of flexible, standardized templates that align with compliance requirements.
- Audit Trails and Logging: Ansible provides logging and auditing capabilities, allowing organizations to track playbook executions, changes made to infrastructure, and any deviations from compliance standards.
- Automated Testing: Ansible playbooks can be integrated into automated testing workflows. This ensures that changes to infrastructure configurations are validated against compliance rules before being applied.
- Policy Enforcement: Ansible playbooks can include tasks specifically designed to enforce compliance policies. These tasks can check configurations, validate security settings, and report or correct non-compliant states.
- Integration with External Tools: Ansible integrates seamlessly with external compliance tools and services. This allows organizations to extend compliance checks beyond Ansible’s capabilities and leverage specialized tools for specific requirements.
- Documentation and Comments: Ansible playbooks should include detailed documentation and comments. This helps in understanding the rationale behind certain configurations and ensures that compliance considerations are well-documented.
- Configuration Drift Detection: Ansible can be used to detect and address configuration drift, ensuring that the actual state of the infrastructure aligns with the defined and compliant state.
By incorporating these features and practices, Ansible facilitates the implementation and enforcement of compliance standards in Infrastructure as Code. It empowers organizations to automate and manage infrastructure configurations while adhering to security, regulatory, and operational compliance requirements.
What solutions does Ansible offer for managing dependencies and versioning?
Ansible offers several solutions for managing dependencies and versioning, ensuring a structured and controlled approach to configuration management and automation:
- Roles and Role Dependencies: Ansible Roles allow you to encapsulate and share functionality, and they can have dependencies on other roles. This provides a modular structure for organizing tasks, handlers, and variables. Role dependencies are defined in the
meta/main.ymlfile of a role. - Ansible Galaxy: Ansible Galaxy is a community hub for sharing Ansible content, including roles. It provides a central repository where roles can be published, discovered, and reused. Roles in Galaxy can specify dependencies on other roles, making it easier to manage complex playbooks.
- Requirements Files: Ansible allows you to define dependencies in a
requirements.ymlfile. This file can list roles and their specific versions, making it easy to manage dependencies and ensure that the same versions are used across environments.Examplerequirements.ymlfile:yamlCopy code--- - name: username.role version: 1.2.3 - Ansible-Galaxy Command: The
ansible-galaxycommand-line tool enables you to install roles and their dependencies listed in arequirements.ymlfile. This simplifies the process of fetching roles and ensuring the correct versions are used.bashCopy codeansible-galaxy install -r requirements.yml - Version Constraints: When specifying role dependencies, you can use version constraints to control which versions of a role are acceptable. For example, you can specify a fixed version, use version ranges, or follow semantic versioning guidelines.Example using a version range:yamlCopy code
- name: username.role version: ">=1.2.3,<=2.0.0" - SemVer Versioning: Ansible roles can follow Semantic Versioning (SemVer) guidelines. This allows for clear versioning semantics, making it easier to understand the impact of changes and ensuring compatibility across different versions.
- Git Repositories as Dependencies: Ansible allows you to specify Git repositories as dependencies for roles. This is useful when roles are not available on Ansible Galaxy, or you need to reference a specific Git commit or branch.Example using a Git repository:yamlCopy code
- name: username.role src: https://github.com/username/ansible-role.git version: "1.2.3"
By leveraging these solutions, Ansible users can efficiently manage dependencies, enforce versioning, and ensure consistent and reproducible configurations across different environments.
How can Ansible be utilized for rolling updates and zero-downtime deployments?
Ansible can be effectively utilized for rolling updates and zero-downtime deployments by leveraging its features for orchestration, parallel execution, and idempotent tasks. Here’s a step-by-step approach:
Rolling Updates:
- Group Hosts: Organize your hosts into groups in your inventory file, separating those that should be updated in each phase of the rolling update.
- Create Playbooks for Each Phase:
- Create separate playbooks or roles for each phase of the rolling update (e.g., pre-update tasks, updating, post-update tasks).
- Use tags to identify tasks specific to each phase.
- Use Serial and Limit: In each playbook, use the
serialkeyword to define the number of hosts updated simultaneously. Additionally, use the--limitoption to specify the group of hosts to update in each phase.Example command:bashCopy codeansible-playbook -i inventory.ini site.yml --limit=group_name - Implement Idempotent Tasks: Ensure that tasks are idempotent so that running the playbook multiple times has the same effect. This minimizes the risk of unintended changes during subsequent runs.
Zero-Downtime Deployments:
- Load Balancer Configuration:
- If applicable, update your load balancer configuration to distribute traffic among both the old and new versions of your application during the deployment.
- Create Rolling Deployment Playbook:
- Create a playbook that handles the deployment of the new version.
- Use
serialto control the number of hosts updated simultaneously, ensuring a gradual rollout.
- Rolling Deployment Tasks:
- Implement tasks that stop and start application services on each host.
- Ensure that the application servers gracefully handle connections during the transition.
- Health Checks:
- Implement health checks or tests in your playbook to verify that the new version of the application is functioning correctly before moving on to the next set of hosts.
- Monitoring and Rollback Plan:
- Set up monitoring to detect issues during deployment.
- Define a rollback plan in case issues are detected. Ansible allows you to easily revert changes by running a playbook that applies the previous version.
- Use Handlers for Service Restart:
- Implement handlers in your roles to restart services only when changes are made. Handlers are only triggered if notified by a task.
tasks: - name: Deploy Application command: /path/to/deploy_script.sh notify: Restart Application handlers: - name: Restart Application service: name: myapp state: restarted
By following these steps and best practices, Ansible can help orchestrate rolling updates and zero-downtime deployments, ensuring a smooth and controlled process with minimal impact on the availability of your services.
Ansible Approach to Configuration Management Challenges
Ansible addresses several challenges in configuration management, offering solutions to streamline and enhance this critical aspect of IT operations. Some key challenges that Ansible helps tackle in configuration management include:
- Consistency Across Environments:
- Challenge: Ensuring consistent configurations across diverse environments can be challenging.
- Ansible Solution: Ansible provides playbooks that define configurations, ensuring consistency across development, testing, and production environments.
- Scalability Issues:
- Challenge: As infrastructure scales, managing configurations manually becomes impractical and error-prone.
- Ansible Solution: Ansible’s automation scales effortlessly, handling configuration management for large and dynamic infrastructures efficiently.
- Versioning and Change Tracking:
- Challenge: Tracking changes to configurations and maintaining versioning is often complex.
- Ansible Solution: Ansible enables version control integration, allowing teams to track changes, roll back to previous configurations, and manage version history.
- Complexity in Scripting:
- Challenge: Creating and managing complex scripts for configuration tasks can be time-consuming and error-prone.
- Ansible Solution: Ansible’s simple, declarative language makes it easy to define configurations without the need for intricate scripting, reducing complexity.
- Cross-Platform Configuration:
- Challenge: Managing configurations across diverse operating systems and platforms presents a compatibility challenge.
- Ansible Solution: Ansible’s agentless architecture allows seamless cross-platform configuration management, supporting a wide range of systems and devices.
- Dependency Management:
- Challenge: Configurations often have dependencies, making it challenging to manage the order of execution.
- Ansible Solution: Ansible intelligently manages dependencies, ensuring configurations are applied in the correct order to avoid conflicts and errors.
- Security and Compliance:
- Challenge: Ensuring configurations comply with security policies and industry regulations is a constant concern.
- Ansible Solution: Ansible helps enforce security policies through automated compliance checks, reducing the risk of misconfigurations and ensuring a secure IT environment.
- Real-Time Configuration Updates:
- Challenge: Applying configuration changes in real-time without disruptions can be a complex task.
- Ansible Solution: Ansible’s push model facilitates real-time updates, allowing administrators to apply changes immediately and efficiently.
- Centralized Configuration Management:
- Challenge: Managing configurations spread across multiple servers in a centralized manner is challenging.
- Ansible Solution: Ansible Tower provides a centralized dashboard for configuration management, offering visibility and control over configurations across the entire infrastructure.
- Lack of Documentation:
- Challenge: Inadequate documentation of configurations leads to difficulties in troubleshooting and understanding the system.
- Ansible Solution: Ansible playbooks serve as self-documenting configurations, improving transparency and aiding in troubleshooting.
By addressing these challenges, Ansible empowers organizations to achieve more efficient, consistent, and secure configuration management across their IT environments.
More Details on the Official website of Ansible
Question: How can Ansible be utilized for rolling updates and zero-downtime deployments?
Answer: Implement rolling updates by organizing hosts, creating phase-specific playbooks, and using Ansible’s serial execution. For zero-downtime deployments, configure load balancers, create deployment playbooks, and employ health checks. Ansible ensures controlled updates, idempotent tasks, and seamless transitions, minimizing service disruptions.
Do you have any further questions on how to use ansible? We also provide training/consulting on Ansible.
You can find Linux Tutorials on this page
You can also find all Video Tutorial on Youtube
Follow us on Facebook Twitter X Reddit Quora Linkedin Tubmblr Youtube